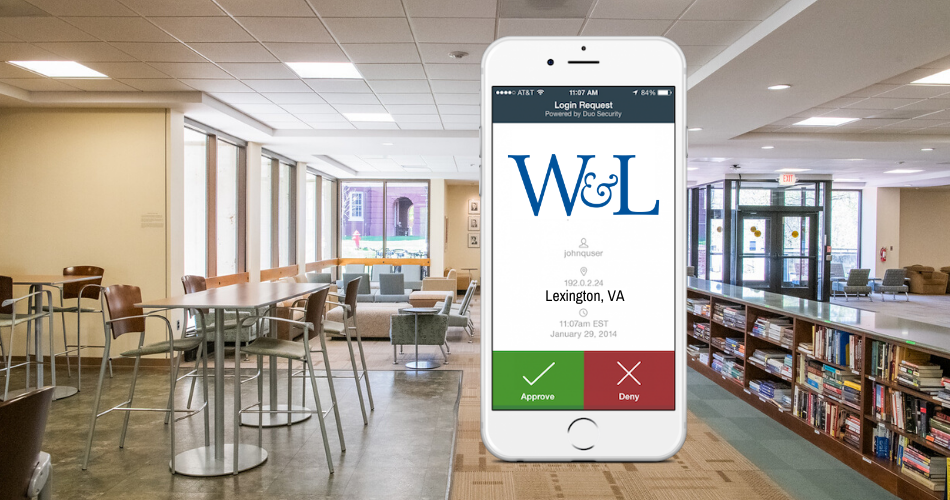
In April, the Office of Student Affairs sent an email to all new students in the class of 2024, instructing them to begin setting up their W&L network and email accounts. In doing so, an unfamiliar step was inserted into the process to help protect the security of their personal information within the University applications they will use while at W&L. The new step involved enrolling in, and activating individual accounts for Duo Multi-Factor Authentication. This new process will eventually be required for all faculty, staff and students.
One month later, 94% of the class of 2024 had successfully enrolled in Duo and used the new tool to access one or more University applications. The process involved having the students download the Duo App (Google Play or App Store) to their mobile phones and step through an intuitive setup engine. The Duo App works in tandem with several University applications (e.g., Outlook Mail, Box, etc.) to keep cyber-criminals from gaining access to personal accounts and private data.
So Why Duo, and Why Now?
Conveying the rationale for requiring a major change to a long-standing operational process, especially one that for many, doesn’t appear broken, can be challenging. Fortunately, we have facts available to offer some clarity.
In 2019, ITS tracked and repaired 107 compromised accounts from faculty, staff and students. Thus far in 2020, we’ve recorded 28 compromised accounts. From these incidents, cyber-criminals were able to gain entry into University applications belonging to individuals by stealing their credentials.
What do we mean by credentials?
Your credentials are the details (often called a “factor”) used to log in to things like Microsoft Outlook Email. Simply put, it’s your username and password. Once a bad actor gains access to this single “factor”, they can log into University applications from anywhere in the world.
What is ITS seeing once an account is compromised?
ITS has tracked a variety of cyber-criminal activities from compromised accounts. Bad actors seek out additional personal information from the affected user that they can use to hack into other accounts like banking apps. They’ve used stolen identities to submit fake invoices or make fraudulent requests for payments. Hacked email accounts have been repeatedly used to release additional phishing emails internally, as well as spread clickable links to executable malware files. Unfortunately, in today’s digital environment, “single factor” credentials simply are not an effective defense.
This is why a multi-factor solution is needed.
To prevent cyber-criminals from gaining access to your University network account, you need more than just your username and password to log in. Duo Security prevents 99.9% of attacks on your accounts by giving you that option of a second factor. With the Duo app on your phone, you can deny access when a fraudulent login attempt is made on your account, should your credentials ever be stolen in the future.
Review our step-by-step Duo enrollment FAQs.
Find out how to get set up with Duo.
Learn more about second factors that can be used with Duo.