UPDATED JULY 7TH
Yesterday, Microsoft started rolling out an emergency Windows patch to address a critical flaw in the Windows Print Spooler service. Details of the vulnerability can be found below. ITS began testing the patch this morning.
Important details for W&L Windows computers
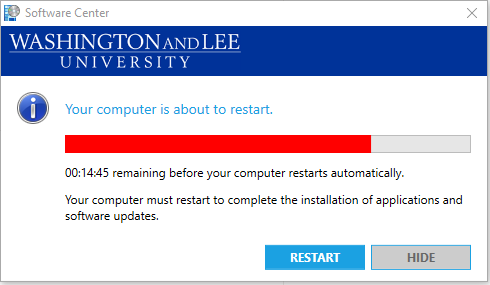
ITS will deploy the patch to all W&L Windows desktops & laptops on Thursday, July 8th at 12:00 noon. If your computer is off, the installation will run the next time your computer is turned on. Once installed, you’ll have 24 hours to reboot before the computer restarts automatically (at approximately noon on Friday, July 9th). You will receive a timer notice (see below) before the automatic restart.
- If you normally turn off your computer at the end of the day, you do not need to do anything different.
- If you typically leave your computer on overnight, please consider rebooting or shutting down your computer at the end of the day on Thursday, July 8th.
- If you do not reboot or shut down your computer after the patch is installed, you will be greeted by a countdown clock on Friday morning listing several hours until the computer will reboot automatically. If you see this message, please reboot your computer at your convenience. Should the timer expire your computer will automatically reboot.
JULY 2ND: ITS is actively monitoring the severe threat posed by a zero-day bug known as PrintNightmare, impacting all versions of Windows. Microsoft has issued warnings that the software vulnerability is being actively exploited by hackers intent on gaining access to enterprise networks. Until a patch becomes available, Microsoft recommends disabling the Windows Print Spooler service and/or disabling remote printing services.
What is a zero-day bug?
A zero-day (also known as 0-day) is a computer-software vulnerability that does not have a patch available to prevent exploitation. Until the vulnerability is mitigated, hackers can exploit it to adversely affect programs, data, additional computers or a network. An exploit directed at a zero-day is called a zero-day exploit, or zero-day attack. Zero-day attacks are a severe threat.
What does this mean for W&L users?
The ITS response to this threat will evolve as updates are received from Microsoft. Current recommendations include “blocking remote attacks by disabling inbound remote printing through a Group Policy” on all managed W&L computers. If your W&L managed computer is functioning as a print server, it may be temporarily disabled. ITS will publish exceptions and/or work-around options, should this become necessary; however, we anticipate that users should still be able to print normally.
Stay tuned to this post for additional information and updates.